Cloud Security Alliance Survey Finds Compromised Credentials Remain Major Data Breach Challenge
April 21, 2016

By Peter Bernstein
Senior Editor
A few years ago, as cyber security issues in general and cloud security ones in particular were starting to gain global publicity, a well-respected security expert told me: “the barbarians are not at the gate they have gotten past it and IDENTITY is the new perimeter.” Hardly a day goes by where that observation is not validated. In fact, the latest confirmation, and the need to better secure identities, comes from Cloud Security Resource co-sponsor the Cloud Security Alliance (CSA) with the release of its new survey titled, “Identity Solutions: Security Beyond the Perimeter,” which was sponsored by cloud security solutions provider Centrify.
In February 2016, the CSA released a report titled, “The Treacherous Twelve: Cloud Computing Top Threats in 2016,” which revealed top concerns of IT security professionals in cloud computing. Just a refresher, it should be remembered that data breaches, account hijacking and malicious insiders all rated as top threats. It was noted in that report that the reasons most often cited for attacks were: a lack of scalable identity access management systems; failure to use multifactor authentication; insufficient password use; and, a lack of ongoing automated rotation of cryptographic keys, passwords and certificates. In short, identity matters really matter. The new report drives this home, with the finding that insufficient identity, credential and access management ranked as the top vulnerability in the latest CSA survey.
“The survey results are insightful into understanding insufficient identity, credential and access management, as it relates to the evolving, increasingly cloud-based enterprise,” said Luciano “J.R.” Santos, Executive Vice President of Research for the CSA. “We hope that organizations and cloud providers can use this information to help gain an understanding of how to protect themselves and their data beyond the perimeter, as they begin to adopt cloud environments.”
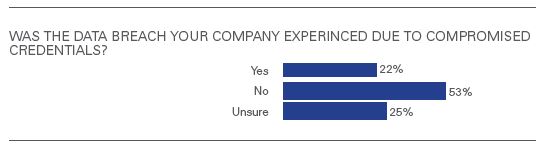
Below is one part of the report readers will find is food for thought, particularly the response that 25 percent of those surveyed were “unsure.”
 Source (News - Alert): CSA 2016 report, Identity Solutions: Security Beyond the Perimeter
Source (News - Alert): CSA 2016 report, Identity Solutions: Security Beyond the Perimeter
Key findings in the 13-page report include:
- Of those who indicated their company reported a data breach, 22 percent of respondents noted the breach was due to compromised credentials. In addition, 65 percent of respondents indicated that the likelihood their company would experience a future breach due to compromised credentials was medium to high.
- Surprisingly, there were no significant differences in security solutions used between respondents who reported a breach and those who either did not report or did not know of a reported breach in their organizations.
- Companies embracing big data solutions consistently adopted more perimeter and identity security solutions.
- 76 percent of internal access control policies extended to outsourced IT, vendors and other third parties.
“The survey findings reiterate that compromised credentials are a leading point of attack used in data breaches,” said Bill Mann, Chief Product Officer for Centrify. “We hope that these findings will encourage organizations to leverage single sign-on, multi-factor authentication, mobile and Mac management, along with privileged access security and session monitoring, in order to minimize attack surfaces, thwart in-progress attacks and achieve continuous compliance. It’s also critical that companies secure internal and external users as well as privileged accounts – and it’s great to see that many organizations are already taking that step and extending access control policies to third parties.”
The last point above is especially one to contemplate as more and more organizations rely on third parties for a variety of capabilities and cloud adoption continues to gather momentum as the home for more and more mission critical applications and services.
Identity really is the new perimeter, and making sure identities are secured and credentials properly validated is an absolutely critical part of the arsenal for keeping cloud activities safe.
Edited by Maurice Nagle
Article comments powered by
 Internet Telephony Magazine
Click here to read latest issue
Internet Telephony Magazine
Click here to read latest issue CUSTOMER
CUSTOMER  Cloud Computing Magazine
Click here to read latest issue
Cloud Computing Magazine
Click here to read latest issue IoT EVOLUTION MAGAZINE
IoT EVOLUTION MAGAZINE




