Verizon 2016 Data Breach Investigations Report Finds Cybercriminals Exploit Human Nature
April 27, 2016

By Peter Bernstein
Senior Editor
Members of the cyber security community are becoming familiar that this time of the year is report season. That is the good news for IT security professionals who want to keep track of all of the malicious activities that are currently in vogue and that they need to be looking at detecting and remediating. And, while all of the reports, considering the breadth and depth of what bad guys are up to and the changing nature of exploits, are worth review, what many consider to be the gold standard of reports, the Verizon 2016 Data Breach Investigations Report (DBIR), has just been released and can be downloaded using the highlighted link. It does not disappoint in terms of its details. What is does do is create a cause for concern.
As the headline says, the news in this year’s DBIR is that cybercriminals are continuing to exploit human nature. Unfortunately, the findings indicate that bad actors, with some sophisticated variations, are relying on familiar attack patterns such as phishing, and increased reliance on ransomware (where data is encrypted and a ransom is demanded) with more than a modicum of success. It shines a bright light on the facts that when it comes to cyber safety we tend to be trusting and open things we should not, and that most organizations and individuals need to be much more cautious. It also highlights the realities that monetization is now a hacking priority and we are doing way too good job of contributing to the cause.
As Verizon (News  - Alert) explains, the DBIR highlights repeating themes from prior year's findings and storylines that continue to play off of human nature, including:
- Alert) explains, the DBIR highlights repeating themes from prior year's findings and storylines that continue to play off of human nature, including:
- Eighty-nine (89) percent of all attacks involve financial or espionage motivations.
- Most attacks exploit known vulnerabilities that have never been patched despite patches being available for months, or even years. In fact, the top 10 known vulnerabilities accounted for 85 percent of successful exploits.
- Sixty-three (63) percent of confirmed data breaches involve using weak, default or stolen passwords.
- 95 percent of breaches and 86 percent of security incidents fall into nine patterns
- Ransomware attacks increased by 16 percent over 2015 findings.
- Basic defenses continue to be sorely lacking in many organizations.
"The Data Breach Investigations Report's increasing importance to businesses, law enforcement and governmental agencies demonstrates a strong desire to stay ahead of cybercrime," said Chris Formant, president of Verizon Enterprise Solutions. "Now more than ever, the collaboration and contributions evidenced in the DBIR from organizations across the globe are required to fully understand the threat landscape. And understanding is the first step toward addressing that threat."
Phishing expeditions top the list and are increasing
As almost every report has revealed, e-mail remains the best way for those with malicious intent to compromise individuals and organizations. In short, phishing expeditions remain all the rage. Plus, passwords, obtained from snooping once a breach has been executed, remain the weakest as they become a passport to hackers to access all types of information that needs to be protected.

Source (News - Alert): Verizon 2016 DBIR
Alarmingly, 30 percent of phishing messages were opened – up from 23 percent in the 2015 report – and 13 percent of those clicked to open the malicious attachment or nefarious link. It gets worse. Verizon notes that previously phishing was only a leading attack pattern for cyber-espionage but has now spread to seven of the nine incident patterns in the 2016 report. The reasons are: “Its popularity has risen because it is an amazingly effective technique and offers attackers a number of advantages such as a very quick time to compromise and the ability to target specific individuals and organizations. “
It is also of consequence that 'Miscellaneous errors' take the No. 1 spot for security incidents. These can include improper disposal of company information, misconfiguration of IT systems, and lost and stolen assets such as laptops and smartphones. In fact, the report points out one of my pet peeves that “Reply to All” is an option and not an obligation and that we all make mistakes. On the latter, 26 percent of these errors involve people mistakenly sending sensitive information to the wrong person.
"You might say our findings boil down to one common theme -- the human element," said Bryan Sartin, executive director of global security services, Verizon Enterprise Solutions. "Despite advances in information security research and cyber detection solutions and tools, we continue to see many of the same errors we've known about for more than a decade now. How do you reconcile that?"
Things are getting dicey
Of increasing concern to Verizon's security researchers is the speed in which cybercrime is committed. In 93 percent of cases, it took attackers minutes or less to compromise systems and data exfiltration occurred within minutes in 28 percent of the cases. Verizon is advising to use the popular slogan in the U.K., to “Mind the Gap.”
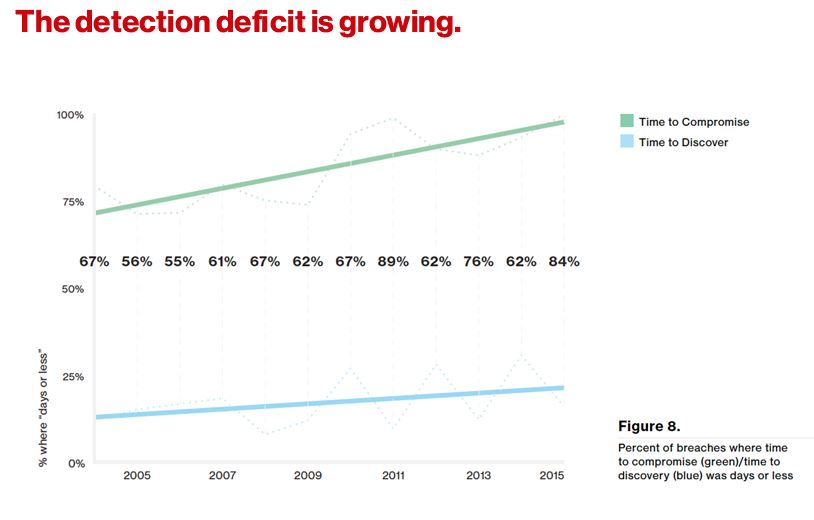
In addition, in case you see a gap in problems covered since IoT compromise did not make this year’s hit parade, the DBIR says - just wait. They point to proof of concept exploits being worked and warn, “it's only a matter of time before a large scale breach impacts mobile and IoT devices, which means organizations should continue to be vigilant about protecting smartphones and IoT devices.”
Another pullout in the report is that Web application attacks climbed to the #1 spot for data breaches, up 33 percent over prior year, and the vast majority (95 percent) were financially motivated.
The rise of the three-pronged attack
So what’s new? The answer in the DBIR is three-prong attacks are new and dangerous to put it mildly. What they entail consists of:
- Sending a phishing email with a link pointing to the malicious website, or a malicious attachment.
- Malware is downloaded onto an individual's PC that establishes the initial foothold, and additional malware can be used to look for secrets and internal information to steal (cyberespionage) or encrypt files for ransom. Many times the malware steals credentials to multiple applications through key logging.
- Use of the credentials for further attacks, for example, to log into third-party websites like banking or retail sites.
"The goal is to understand how the cybercriminals operate," said Sartin. "By knowing their patterns, we can best prevent, detect and respond to attacks."
Basics needed to be followed
It is beginning to sound like a broken record since the advice on how to improve an organization’s security posture really has not deviated in the past few years. As Verizon says, its researchers believe that basic, well-executed measures continue to be more important than complex systems. Here is what they advise:
- Know what attack patterns are most common for your industry.
- Utilize two-factor authentication for your systems and other applications, such as popular social networking sites.
- Patch promptly.
- Monitor all inputs: Review all logs to help identify malicious activity.
- Encrypt your data: If stolen devices are encrypted, it's much harder for attackers to access the data.
- Train your staff: Developing security awareness within your organization is critical especially with the rise in phishing attacks.
- Know your data and protect it accordingly. Also limit who has access to it.
"This year's report once again demonstrates that there is no such thing as an impenetrable system, but often times even a basic defense will deter cybercriminals who will move on to look for an easier target," added Sartin.
In fact, you might wish to print out as a reminder the below graphic.

Finally, my reference to this being the Gold Standard is not just a reflection of my inbox which is already flooded with several dozen comments from various security vendors from around the world. Rather, it is a testament to Verizon’s depth of knowledge and ability to track and analyze things.
Now in its ninth year of publication, the DBIR analyzes more than 2,260 confirmed data breaches and more than 100,000 reported security incidents. The report addresses more than 10,000 breaches and nearly 300,000 security incidents that have occurred over more than 11 years, and includes security incidents that don't result in breaches, in order to offer a better survey of the cybersecurity landscape. But the real value is that Verizon is among 67 global organizations that contributed data and analysis to this year's report.
Edited by Stefania Viscusi
Article comments powered by
 Internet Telephony Magazine
Click here to read latest issue
Internet Telephony Magazine
Click here to read latest issue CUSTOMER
CUSTOMER  Cloud Computing Magazine
Click here to read latest issue
Cloud Computing Magazine
Click here to read latest issue IoT EVOLUTION MAGAZINE
IoT EVOLUTION MAGAZINE




