Human Error Is to Blame for Most Breaches
June 06, 2016
Each year, as companies implement the latest security technologies, attackers develop and launch new tactics, techniques, and procedures to circumvent those technologies. While investment in security defense and detection technologies is an essential component to building an effective defense-in-depth strategy, the reality is that most breaches can be traced back to human error. BakerHostetler’s 2016 Data Security Incident Response Report, looks at the more than 300 incidents that the firm handled in 2015 to identify the top causes. Identifying and understanding the constantly evolving causes of security incidents, which vary among industries, helps the firm to not only better advise organizations on how to proactively become “compromise ready,” but also enables the use of “lessons learned” to help organizations effectively respond to incidents when they do occur.
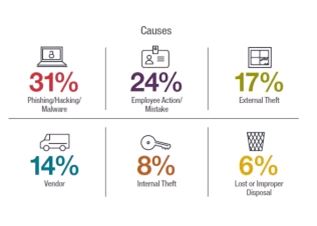
The 2015 report identified human error as the leading cause of incidents (37 percent), followed by phishing/malware (25 percent), external theft of a device (22 percent), and employee theft (16 percent). This year, however, phishing/hacking/malware took the top spot, accounting for approximately 31 percent of incidents. The other top causes were employee action/mistake (24 percent), external theft (17 percent), vendors (14 percent), internal theft (8 percent), and lost or improper disposal (6 percent). From an industry perspective, these top causes were relatively consistent with phishing/hacking/malware as the leading cause, with the exception of healthcare, in which human error remained the top cause of incidents by a significant margin.
Taking a Closer Look
When a closer look at the underlying issues that allowed the phishing/hacking/malware incidents to occur is taken, the incidents could often be attributed to human error in some way. Attackers are increasingly relying on phishing emails to bypass an organization’s next-generation layered network perimeter, which makes direct penetration more difficult for the attackers. Phishing is a low-cost but highly effective attack vector to gain access to an otherwise well-secured network. Social media, such as LinkedIn (News - Alert) and Facebook, provide a treasure trove of information for attackers to identify and target employees with carefully crafted phishing emails. Even in large-scale breaches involving thousands of systems across the globe, the initial attack vector was rarely a sophisticated exploitation of a zero-day vulnerability. Rather, the initial vector was more often a spear-phishing email that tricked an employee or vendor into providing his or her remote-access credentials or opening an attachment containing a malicious payload. Even when phishing is not the initial vector, many of the hacking and malware incidents can still be traced to human error, such as failure to patch known vulnerabilities.
Many incidents in the “external theft” category can also be traced to human error, such as employees and staff leaving laptops and mobile devices in unlocked cars and other unsecure places. Internal theft of devices or documents containing sensitive information often occurs when employees are given access to systems and information beyond that which is necessary for the employee to perform his or her job duties, or when access is not removed immediately upon an employee’s termination or reassignment. The “employee action/mistake” category includes incidents such as when an employee emails sensitive data to an unintended person or developers inadvertently configure a database containing sensitive data to be Internet-facing and searchable through Google (News - Alert). The “lost or improper disposal” category can be, almost by definition, attributed to human error. Accordingly, when you consider the role human error plays in each of these categories of incidents, human error is a factor well over half the time.
What Does This Mean for Organizations?
Failing to address the human component of data protection can negate many of the next-generation defense-in-depth technologies in which organizations are investing handsomely. So what should organizations do? While there is no one-size-fits-all approach, addressing the human component of data protection requires implementation of several technical, administrative, and procedural safeguards, including:
- Data security awareness and training: Many incidents resulting from human error, such as disposing of devices without first wiping the data, can be effectively addressed by training and awareness programs for employees and vendors who handle sensitive information. Training employees on the organization’s information security policies and procedures should be part of the onboarding process and should be included in periodic training. These programs should be continuously updated to address the constantly evolving threat landscape as well as organizational changes impacting data privacy and security.
- Simulated phishing programs: Implementing a program that simulates phishing attacks on employees and vendors can be effective at training users on how to identify and avoid phishing messages. These programs help organizations measure the existing baseline susceptibility of employees, identify those users that need additional training, and measure the organization’s progress toward reducing user click rates. Regulators are acutely aware that phishing attacks are the leading cause of external data breaches, and organizations having a mature and well-documented anti-phishing program will be better positioned to withstand regulatory scrutiny following a breach.
- Full encryption of devices and portable storage: The frequency of lost or stolen devices containing sensitive information will continue to rise as more users store sensitive organizational data on their laptops, mobile devices, and portable storage devices. Most state breach notification laws provide a “safe harbor” against compulsory notification of breaches where the data is protected by encryption. As such, organizations should seek to implement full encryption of all devices that may contain sensitive data. Indeed, many regulators expect it and now view the lack of encryption as per se unreasonable security.
- Data loss prevention software: Sensitive data can be leaked outside an organization by inadvertent mistake or malicious intent. Data loss prevention software is designed to prevent users from sending sensitive data outside the corporate network without authorization.
- Access rights and privileges: Organizations can substantially reduce their attack surface and the likelihood for human error causing a data security incident by implementing and maintaining policies and procedures based on the least-privilege principle. The least-privilege principle means that users should be given only the minimum access to sensitive data necessary to perform a job function and that access should only be granted for the minimum time necessary. While the least-privilege principle is an age-old security management principle, organizations often fail to remain diligent in monitoring and limiting users’ privileges as employees’ roles and the systems for which they truly need access change over time.
About the Author

Will Daugherty is counsel with BakerHostetler’s Privacy and Data Protection team. Based in Houston, he helps clients develop and implement information security compliance programs and incident response plans, and to respond to data breaches and other security incidents.
The BakerHostetler Data Security Incident Response Report can be found here.
Article comments powered by
 Internet Telephony Magazine
Click here to read latest issue
Internet Telephony Magazine
Click here to read latest issue CUSTOMER
CUSTOMER  Cloud Computing Magazine
Click here to read latest issue
Cloud Computing Magazine
Click here to read latest issue IoT EVOLUTION MAGAZINE
IoT EVOLUTION MAGAZINE




