GSM calls are protected but the mechanism is relatively weak. In a month or so the codebook will be in the public domain and all hackers will need is a high-end notebook. But there’s also a high-end solution that does end-to-end encryption over data-enabled networks.
A survey conducted amongst 250 senior executives in the United States by ABI Research (News - Alert) indicates that the majority of large and medium businesses are failing to adequately protect themselves against the growing threat of mobile voice call interception, which can lead to the loss of sensitive and confidential corporate information.
One alarming fact that emerged was that 55 percent of respondents in IT roles thought that their organization had implemented mobile voice call encryption solutions but on further investigation only 18 percent had actually done so.
Effective email security has become routine, but the research showed that most businesses do not apply anything like the same level of security to cell phone calls.
The problem was highlighted in August 2009 when German hackers announced a project to create a code table that cracks the encryption of GSM calls, used in 80 percent of the world’s cell phone calls. This codebook will probably be freely available within the next 6 months.
In the light of that development Cellcrypt, a provider of technology to secure mobile voice calls, commissioned the research. Governments and enterprises use the company’s solutions worldwide and the results of the survey would seem to validate their deployment.
The technology is impressive and, as shown in figure 1 below, the solution does not rely on a secure air interface, which was and still is the conventional mechanism. Instead, security is enabled end-to-end using EMCP (Encrypted Mobile Content Protocol) client software in both devices.
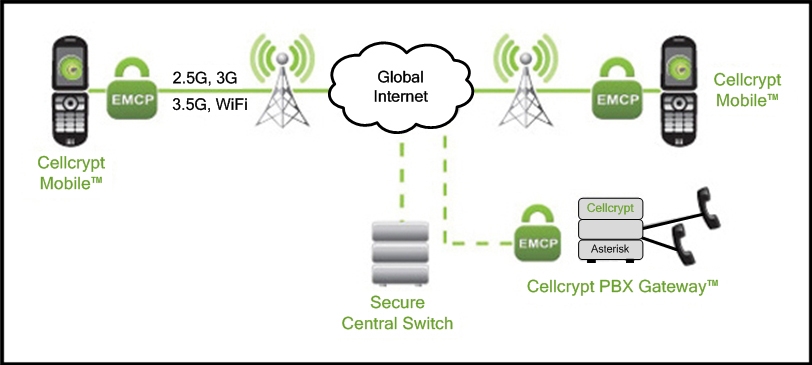
EMCP is an IP-based technology that enables the secure delivery of data between mobile devices over wireless networks. This means that it’s a VoIP call, but for obvious reasons Cellcrypt doesn’t use that term. One doesn’t associate VoIP with security.
Cellcrypt uses standard encryption technologies that include: RSA (News - Alert) 2048 bit and AES 256 bit encryption; DH and RSA algorithms for key exchange; SHA512 and MD5 for hashing; and DSA and RSA to authenticate data.
The solution uses the data channel of cellular networks as well as Wi-Fi. After the base station they go over the Internet. A secure central switch hosted by Cellcrypt sets up calls between mobiles. The PBX (News - Alert) gateway is used to direct calls to landline devices.
The company’s products are compliant with the FIPS 140-2 standard administered by the US National Institute of Standards and Technology (NIST) and right now they are optimized to run on Nokia Symbian (News - Alert) and BlackBerry smartphones.
The annual service isn’t cheap, but then it’s not designed for mobile workforces. The target audience is management and professionals who need to communicate sensitive information and since deployment stops calls being intercepted it could turn out to be a bargain. But then one would never know.
 Internet Telephony Magazine
Click here to read latest issue
Internet Telephony Magazine
Click here to read latest issue CUSTOMER
CUSTOMER  Cloud Computing Magazine
Click here to read latest issue
Cloud Computing Magazine
Click here to read latest issue IoT EVOLUTION MAGAZINE
IoT EVOLUTION MAGAZINE




